Do you know that your organization is vulnerable to serious network security threats?
With organizations relying more and more on network technologies, security has become a key concern in the modern business environment. Although large businesses are more susceptible to network threats, small and medium sized firms are not safe from security risks. It only takes a small security lapse for a small business to become the target of eavesdroppers and hackers.
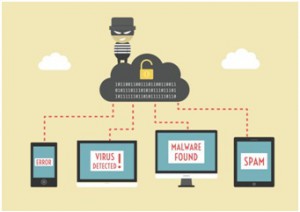
Keeping this in mind, you need to adopt a robust data security strategy to protect your business from reputational and financial damages. To make a well defined data security strategy, let’s have a look at common network security threats that you particularly need to address.
Malicious Programs
Malicious programs are unstructured threats that are usually initiated by people with limited or developing skills. These programs can enter and affect all the devices connected over the same network which may lead to system failure or other network problems.
While the original purpose of the program might not be malicious, the result can be loss of user access, decline in productivity, reputational damages, and a loss in revenues.
Physical Access
The trend of Bring Your Own Device (BYOD) has led to an increase in data breaches. While modern compact devices’ portability offers convenience, their handiness makes them highly vulnerable to data theft and losses. In case of theft, even the most secure device could fail to save your data from the ill intentions of an intruder.
It is essential that you protect your network with high-end access control system to prevent unauthorized people from breaking into the network.
Insider Threats
Sometimes your internal employees can make your business environment vulnerable to threats. By downloading unauthorized programs, they might invite unintentional threats that could access company’s assets without your knowledge.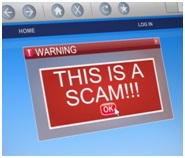
Network security threats will continue to increase with the growth of seemingly endless pool of devices and technological tools. In the wake of technological developments and the industry’s growing shift towards technological approaches, make sure that you fully understand the implications of flawed network management practices. With a secure network, not only can you protect the integrity of your business, but also ensure adherence to best practices and regulatory requirements.
Consider moving to an intranet/extranet solution in your next corporate budget to create a secure and compliant business environment. To purchase the intranet and extranet tool, get in touch with us online or call us at 877-765-2655.
Leave a Reply
You must be logged in to post a comment.